Internet Protocols (TCP/IP and UDP) are fundamental for communication across the internet. Here's a breakdown of each:
1. TCP/IP (Transmission Control Protocol/Internet Protocol)
TCP/IP is a suite of communication protocols used to interconnect network devices on the internet. It includes various layers that define how data is transmitted and received across networks. Here's a breakdown of the key protocols within this suite:
Transmission Control Protocol (TCP): TCP ensures reliable, ordered, and error-checked delivery of data between applications. It breaks data into packets and reassembles them at the destination. TCP is connection-oriented, meaning a connection must be established before data is transmitted, and it guarantees the delivery of data in the correct order. If any packet is lost, TCP will retransmit it.
Key Characteristics:
Reliable data transfer
Guarantees order and correctness
Acknowledgements (ACK) for successful delivery
Retransmissions in case of errors
Flow control and congestion management
Internet Protocol (IP): IP handles the addressing and routing of data. It ensures that each packet of data has a destination address and can be routed across the internet. There are two versions: IPv4 and IPv6. IPv4 is more common, but IPv6 is growing due to the exhaustion of IPv4 addresses.
Key Characteristics:
Unreliable (no guarantee of packet delivery)
Routes data packets across different networks using IP addresses
Works with both IPv4 and IPv6
IP Addressing: Every device connected to the internet is assigned an IP address, which is used to uniquely identify it.
2. UDP (User Datagram Protocol)
UDP is a simpler, connectionless protocol compared to TCP. It is used for applications where speed is more critical than reliability. Unlike TCP, UDP does not establish a connection before data transfer, nor does it ensure that packets are received or in the correct order. It sends packets as datagrams without the need for acknowledgments or retransmissions.
Key Characteristics:
Connectionless (no handshake before transmission)
Unreliable (no guarantee of delivery or order)
Faster than TCP because it doesn't have the overhead of error-checking or retransmissions
Suitable for applications like video streaming, online gaming, and VoIP where real-time data delivery is crucial and occasional data loss is acceptable
Key Differences Between TCP and UDP:
| Feature | TCP | UDP |
| Connection | Connection-oriented | Connectionless |
| Reliability | Reliable (guarantees delivery) | Unreliable (no guarantee of delivery) |
| Speed | Slower (due to error checking) | Faster (no error checking) |
| Error Checking | Extensive error checking | Minimal error checking |
| Use Cases | Web browsing, email, file transfer | Video streaming, gaming, DNS queries |

What are Network Protocols?
A network protocol is a set of rules and conventions that govern how data is transmitted and received over a network. Protocols define the format, timing, sequencing, and error-checking of communication between devices on a network. In essence, they establish the standards and guidelines that ensure reliable, secure, and efficient data exchange.
Key Characteristics of Network Protocols:
Communication Rules: They specify how devices on a network should format and send data so that other devices can understand it.
Error Handling: Many protocols include mechanisms to check for and correct errors in data transmission.
Data Structure: They determine the format of data packets, such as headers (which contain routing and control information) and payloads (which contain the actual data).
Flow Control: They manage how much data can be sent at a time to avoid overwhelming network resources.
Security: Many protocols include encryption and other security measures to protect data from unauthorized access or tampering.
Types of Network Protocols
Network protocols come in various types, including:
Transmission Protocols: These manage how data is sent across networks (e.g., TCP and UDP).
Routing Protocols: These determine how data is routed from source to destination across networks (e.g., IP).
Application Protocols: These govern how applications communicate over networks (e.g., HTTP, FTP, DNS).
Security Protocols: These protect data from unauthorized access (e.g., SSL/TLS, IPSec).
Examples of Common Network Protocols:
HTTP (Hypertext Transfer Protocol): Governs how web browsers request and receive content from web servers.
FTP (File Transfer Protocol): Used for transferring files between a client and a server over a network.
SMTP (Simple Mail Transfer Protocol): Used for sending emails between servers.
DNS (Domain Name System): Resolves domain names (like
example.com) to IP addresses.IP (Internet Protocol): Routes data packets across networks.
TCP (Transmission Control Protocol): Ensures reliable, error-free delivery of data packets.
Why Do Network Protocols Matter?
Consistency and Standardization:
Protocols allow different devices (from different manufacturers) to communicate effectively and reliably.
They ensure that systems can exchange data using a common language, making interoperability possible.
Reliable Data Transfer:
- Network protocols like TCP ensure that data is delivered correctly and in order, preventing errors or lost information.
Efficient Communication:
Protocols manage the flow of data, reducing network congestion and ensuring that devices don’t overwhelm each other.
They provide mechanisms for managing bandwidth and reducing delays.
Security:
Many protocols provide built-in encryption, authentication, and data integrity features, making communication over the internet safer.
Security protocols (like HTTPS) are critical for protecting sensitive data, such as passwords, credit card numbers, and personal information.
Scalability:
- Protocols like IP make it possible for networks to grow by defining how devices are identified (via IP addresses) and how data is routed across large, complex networks like the internet.
Network Management:
Protocols provide the foundation for managing and maintaining network health. They enable troubleshooting, performance monitoring, and fault isolation.
Routing and management protocols ensure that data is delivered in the most efficient and reliable manner.
Optimizing Network Performance:
- Protocols define how data is compressed, segmented, and transmitted efficiently, improving overall network performance and reducing resource consumption.
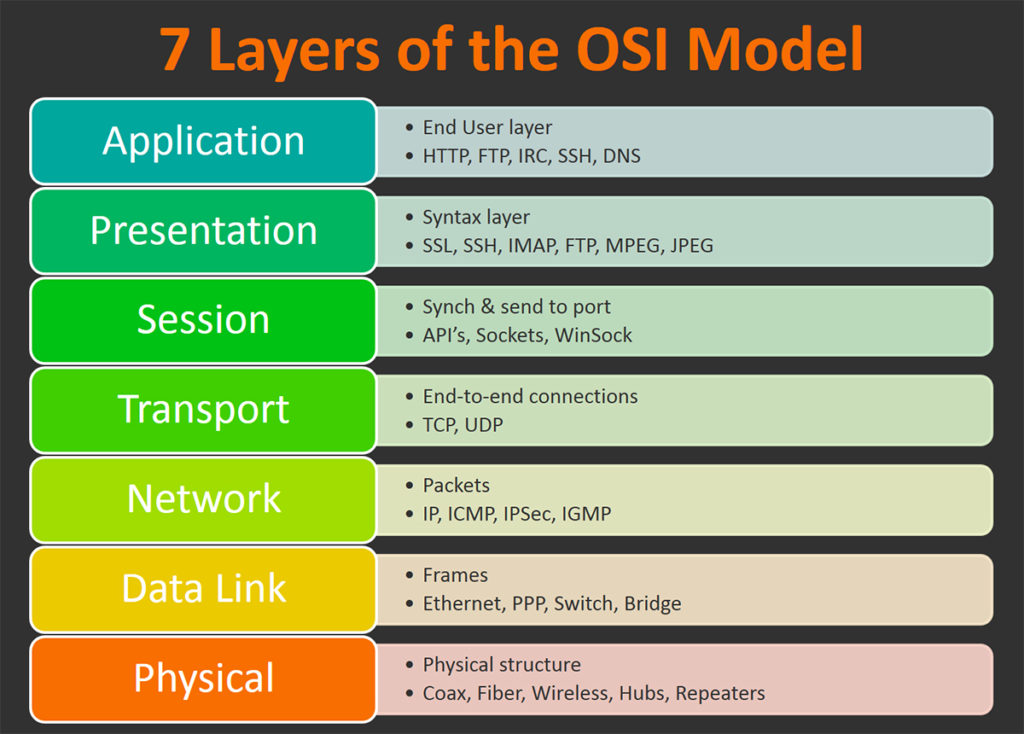
The OSI Model and Its Protocols
The OSI (Open Systems Interconnection) model is a conceptual framework used to understand and describe how different network protocols interact and work together to enable communication in a network. It divides the process of communication into seven distinct layers, each with its specific function and protocols. These layers allow for standardization, interoperability, and troubleshooting of network communications.
The 7 Layers of the OSI Model
Layer 1: Physical Layer
Function: Deals with the physical connection between devices. It defines how data is transmitted over the physical medium, such as electrical signals, light pulses, or radio waves.
Protocols/Technologies:
Ethernet (for wired connections)
Wi-Fi (for wireless connections)
USB (Universal Serial Bus)
Bluetooth
Devices:
Network cables (e.g., fiber optic, copper)
Hubs, repeaters
Layer 2: Data Link Layer
Function: Ensures reliable transfer of data over the physical layer by framing and addressing data packets. It also handles error detection and correction.
Protocols:
Ethernet (for local area networks)
PPP (Point-to-Point Protocol) (used in direct connections)
Frame Relay
MAC (Media Access Control)
Devices:
Switches
Bridges
Network Interface Cards (NICs)
Layer 3: Network Layer
Function: Responsible for determining the best path for data to travel across networks. It handles logical addressing and routing of data between devices on different networks.
Protocols:
IP (Internet Protocol): Both IPv4 and IPv6 are used for addressing and routing.
ICMP (Internet Control Message Protocol): Used for diagnostic tools like ping.
ARP (Address Resolution Protocol): Resolves IP addresses to MAC addresses.
Devices:
- Routers
Layer 4: Transport Layer
Function: Ensures the reliable transfer of data between two devices. It provides end-to-end communication, error recovery, and flow control.
Protocols:
TCP (Transmission Control Protocol): Reliable, connection-oriented.
UDP (User Datagram Protocol): Connectionless and faster, but unreliable.
Devices:
- No specific hardware at this layer, but it is implemented by the operating system's networking stack.
Layer 5: Session Layer
Function: Manages sessions or connections between applications on different devices. It establishes, maintains, and terminates communication sessions.
Protocols:
NetBIOS (Network Basic Input/Output System)
RPC (Remote Procedure Call)
SMB (Server Message Block)
Devices:
- None (handled by software)
Layer 6: Presentation Layer
Function: Translates data into a format that is understandable by the receiving application. It may include data encryption, compression, and translation between different data formats.
Protocols:
TLS/SSL (Transport Layer Security / Secure Sockets Layer) for encryption
JPEG, GIF (image formats)
MIME (Multipurpose Internet Mail Extensions) for email
ASCII, EBCDIC (character encoding)
Devices:
- None (handled by software)
Layer 7: Application Layer
Function: The topmost layer, which interacts directly with user applications. It provides services like file transfers, email, web browsing, etc.
Protocols:
HTTP (Hypertext Transfer Protocol) for web browsing
FTP (File Transfer Protocol) for file transfer
SMTP (Simple Mail Transfer Protocol) for email
DNS (Domain Name System) for resolving domain names to IP addresses
POP3/IMAP for email retrieval
Devices:
- End-user devices like computers, smartphones, etc.
Key Points About the OSI Model:
Each layer has a specific function and is independent of the others, but all layers work together to achieve successful communication between devices.
The model is conceptual and does not specify exact protocols; rather, it categorizes protocols that serve each layer's specific purpose.
When data is transmitted, it travels from the top (Application) layer down to the bottom (Physical) layer, and when received, it travels back up from the Physical layer to the Application layer.
Why the OSI Model Matters
Standardization: The OSI model provides a standardized framework that helps different network hardware and software to communicate with each other.
Interoperability: Devices from different vendors can communicate if they follow the same protocols at each layer of the OSI model.
Troubleshooting: The OSI model helps network engineers and IT professionals diagnose network issues by isolating problems to specific layers.
Development: It guides developers in creating network communication systems, ensuring that software and protocols can interact seamlessly across layers.
Comparison with the TCP/IP Model
While the OSI model is more detailed and conceptual, the TCP/IP model is often used in practice because it's the basis for most internet protocols. The TCP/IP model has only 4 layers:
Link Layer (combines the OSI Physical and Data Link layers)
Internet Layer (equivalent to OSI Network layer)
Transport Layer (same as OSI Transport layer)
Application Layer (combines OSI's Session, Presentation, and Application layers).
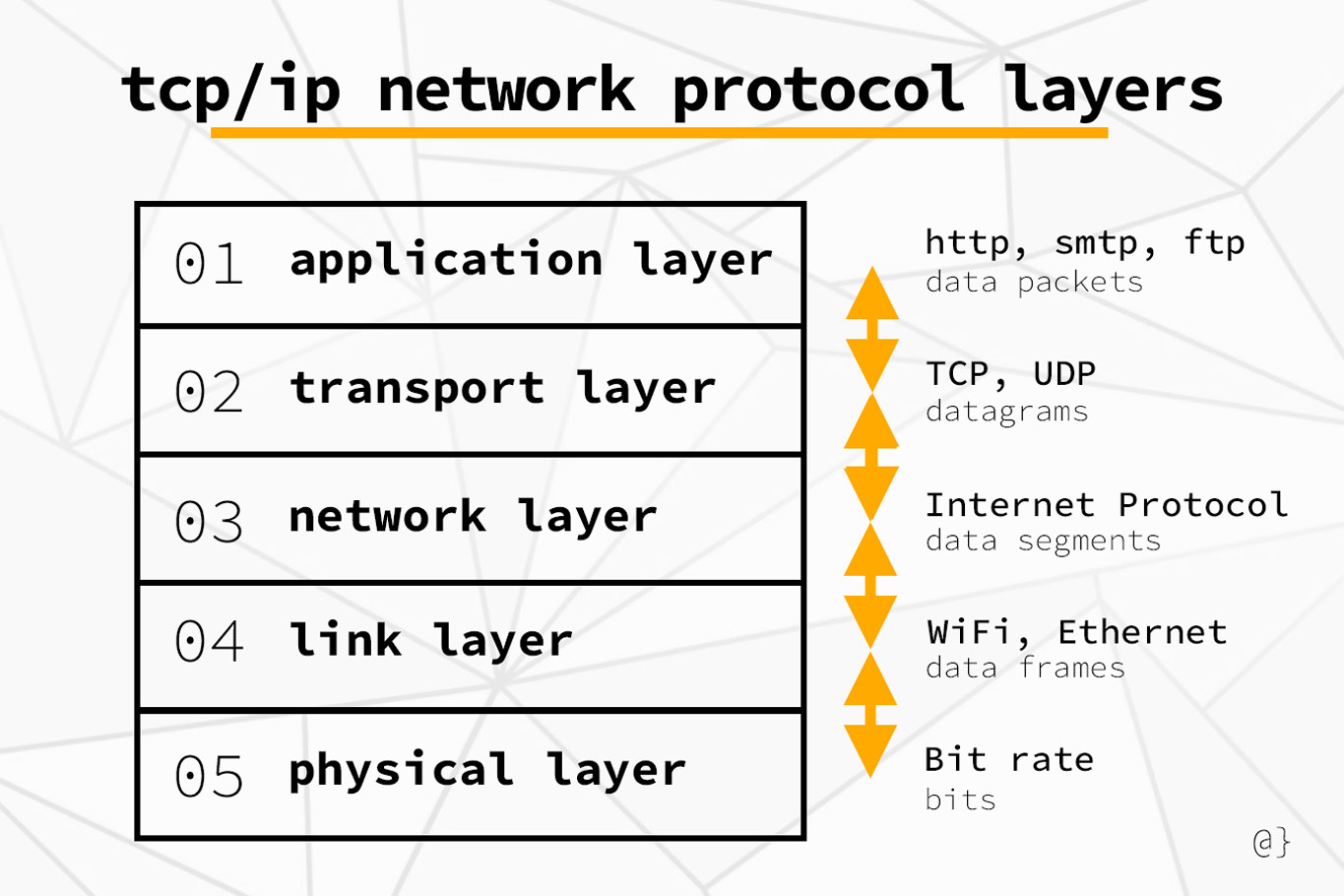
Basic Overview of TCP/IP
The TCP/IP (Transmission Control Protocol/Internet Protocol) model is the foundational suite of protocols that powers the internet and most modern computer networks. It defines how data is transmitted and routed between devices across networks and the internet. The model's primary purpose is to ensure reliable communication between devices, whether they are on a local network or connected over vast distances (like the internet).
The Layers of the TCP/IP Model
The TCP/IP model consists of 4 layers, each of which focuses on specific tasks related to data communication. Here's an overview of each layer and the protocols associated with it:
1. Link Layer (Network Interface Layer)
Purpose: This layer is responsible for communication between devices on the same local network or directly connected networks. It defines how data is physically transmitted over different types of media, such as Ethernet cables, Wi-Fi, or fiber optics.
Functionality:
Handles the physical addressing (e.g., MAC addresses)
Deals with the transmission of raw data packets
Error detection and correction for data transmission over the physical network medium
Protocols/Technologies:
Ethernet (wired network communication)
Wi-Fi (wireless communication)
PPP (Point-to-Point Protocol)
ARP (Address Resolution Protocol): Resolves IP addresses to MAC addresses
Devices:
Network Interface Cards (NICs)
Switches
Routers
2. Internet Layer
Purpose: The Internet layer is responsible for routing data across networks. It ensures that data packets can travel from one network to another, often over the internet, by assigning logical addresses (IP addresses) and determining the best route for the data.
Functionality:
Routes data packets to their destination across different networks
Breaks data into smaller units (packets) and assigns each packet a source and destination address
Handles logical addressing and routing
Protocols:
IP (Internet Protocol): The core protocol for addressing and routing. Includes:
IPv4 (Internet Protocol version 4): Most widely used; uses 32-bit addresses.
IPv6 (Internet Protocol version 6): The newer version with 128-bit addresses, designed to overcome IPv4 address limitations.
ICMP (Internet Control Message Protocol): Used for diagnostic purposes (e.g., ping command) and error reporting.
ARP (Address Resolution Protocol): Resolves IP addresses to MAC addresses.
Devices:
Routers
Gateways
3. Transport Layer
Purpose: The transport layer is responsible for ensuring reliable and accurate communication between two devices or applications. It provides end-to-end data delivery services and error handling.
Functionality:
Breaks large messages into smaller packets for easier transmission
Ensures that data is delivered in the correct order
Provides error detection and recovery mechanisms
Manages flow control to prevent network congestion
Protocols:
TCP (Transmission Control Protocol):
Connection-oriented protocol: A connection must be established before data transmission.
Reliable: Guarantees data delivery, retransmits lost packets, and ensures data is received in the correct order.
Includes flow control, error detection, and congestion management.
UDP (User Datagram Protocol):
Connectionless protocol: No formal connection is established before data transmission.
Unreliable: Does not guarantee delivery, order, or error correction.
Faster than TCP because of the lack of error checking and acknowledgment mechanisms. Ideal for real-time applications (e.g., streaming, gaming).
4. Application Layer
Purpose: This layer is responsible for providing network services directly to end-user applications. It defines the protocols that enable software applications to communicate over a network.
Functionality:
Provides services such as email, file transfer, and web browsing
Specifies protocols for specific applications, such as retrieving web pages or sending emails
Enables communication between user applications (e.g., web browsers, email clients)
Protocols:
HTTP (Hypertext Transfer Protocol): Used for web browsing.
FTP (File Transfer Protocol): Used for transferring files between computers.
SMTP (Simple Mail Transfer Protocol): Used for sending emails.
POP3 (Post Office Protocol 3) and IMAP (Internet Message Access Protocol): Used for receiving emails.
DNS (Domain Name System): Resolves domain names (e.g.,
example.com) to IP addresses.DHCP (Dynamic Host Configuration Protocol): Assigns IP addresses to devices on a network automatically.
Why TCP/IP Matters
Interoperability: TCP/IP enables different devices, operating systems, and network architectures to communicate and exchange data. It provides a standardized method for data transmission across the globe, ensuring compatibility.
Scalability: The Internet Protocols (IP) allow for the global expansion of networks. With millions of devices connected to the internet, TCP/IP protocols make sure that they can communicate seamlessly, handling large-scale networks.
Reliability: The transport layer, specifically TCP, ensures that data is reliably delivered without loss or corruption. Applications like web browsing and email depend on the robustness of TCP for reliable data transmission.
Efficiency: UDP allows for faster communication, making it ideal for real-time applications like video conferencing or online gaming where speed is more important than guaranteed delivery.
Security: Security protocols, such as TLS/SSL, can be implemented on top of the TCP/IP stack to encrypt data and protect communications from unauthorized access or tampering.

